What is Cross-Site Scripting Attack:-
Cross-site scripting, or XSS, involve
a website including unintended Javascript code which is subsequently passes on
to users who then execute that code via their browsers. A harmless example of
this is :- alert(‘XSS’)
 Cross-Site Scripting (XSS) attacks are a type of injection, in
which malicious scripts are injected into otherwise benign and trusted
websites. XSS attacks occur when an attacker uses a web application to send
malicious code, generally in the form of a browser side script, to a different
end user. Flaws that allow these attacks to succeed are quite widespread and
occur anywhere a web application uses input from a user within the output it
generates without validating or encoding it.
Cross-Site Scripting (XSS) attacks are a type of injection, in
which malicious scripts are injected into otherwise benign and trusted
websites. XSS attacks occur when an attacker uses a web application to send
malicious code, generally in the form of a browser side script, to a different
end user. Flaws that allow these attacks to succeed are quite widespread and
occur anywhere a web application uses input from a user within the output it
generates without validating or encoding it.
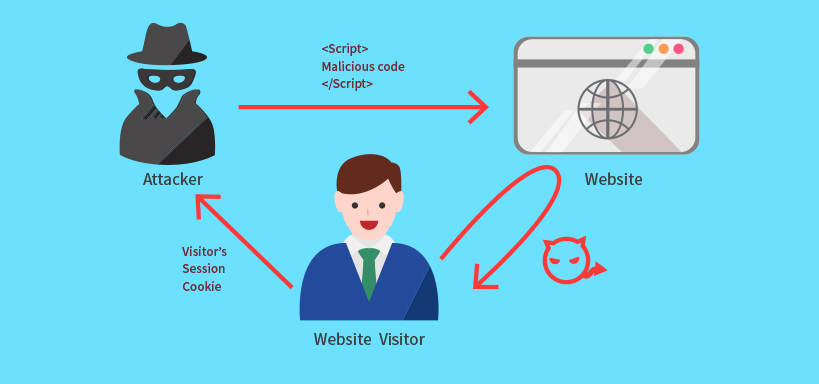
An attacker can use
XSS to send a malicious script to an unsuspecting user. The end user’s browser
has no way to know that the script should not be trusted, and will execute the
script. Because it thinks the script came from a trusted source, the malicious
script can access any cookies, session tokens, or other sensitive information
retained by the browser and used with that site. These scripts can even rewrite
the content of the HTML page. For more details on the different types of XSS
flaws.
- Malicious JavaScript has access to all the
objects that the rest of the web page has access to. This includes access
to the user’s cookies. Cookies are often used to store session tokens. If
an attacker can obtain a user’s session cookie, they can impersonate that
user, perform actions on behalf of the user, and gain access to the user’s
sensitive data.
- JavaScript can read the browser DOM and make
arbitrary modifications to it. Luckily, this is only possible within the
page where JavaScript is running.
- JavaScript can use the XML Http
Request object to send HTTP requests with arbitrary
content to arbitrary destinations.
- JavaScript in modern browsers can use HTML5 APIs.
For example, it can gain access to the user’s geolocation, webcam,
microphone, and even specific files from the user’s file system. Most of
these APIs require user opt-in, but the attacker can use social
engineering to go around that limitation.
The above, in combination with social
engineering, allow criminals to pull off advanced attacks including cookie
theft, planting trojans, keylogging, phishing, and identity theft. XSS
vulnerabilities provide the perfect ground to escalate attacks to more serious
ones. Cross-site Scripting can also be used in conjunction with other types of
attacks, for example, Cross-Site
Request Forgery (CSRF).There are several types of Cross-site
Scripting attacks: stored/persistent
XSS, reflected/non-persistent
XSS, and DOM-based XSS. You can read more about them in an article titled Types of XSS.
How Cross-site Scripting Work :-
There are two stages to a typical XSS
attack:
1. To run malicious JavaScript code in a victim’s browser, an attacker must
first find a way to inject malicious code (payload) into a web page that the
victim visits.
2. After that, the victim must visit the web page with the malicious code.
If the attack is directed at particular victims, the attacker can use social
engineering and/or phishing to send a malicious URL to the victim.
Cross-Site Scripting (XSS) attacks occur when:-
1. Data
enters a Web application through an untrusted source, most frequently a web
request.
2. The
data is included in dynamic content that is sent to a web user without being
validated for malicious content.
The malicious content sent to the web browser often
takes the form of a segment of JavaScript, but may also include HTML, Flash, or
any other type of code that the browser may execute. The variety of attacks
based on XSS is almost limitless, but they commonly include transmitting
private data, like cookies or other session information, to the attacker,
redirecting the victim to web content controlled by the attacker, or performing
other malicious operations on the user’s machine under the guise of the
vulnerable site.
Types of Cross-Site Scripting (XSS):-
1.
Self XSS: These attacks are also not persisted and are usually
used as part of tricking a person into running the XSS themselves.
2.
Persistent(Stored)
XSS: These attacks are persisted, or saved, and then executed when a page is
loaded to unsuspecting users. Stored attacks are
those where the injected script is permanently stored on the target servers,
such as in a database, in a message forum, visitor log, comment field, etc. The
victim then retrieves the malicious script from the server when it requests the
stored information. Stored XSS is also sometimes referred to as Persistent or
Type-I XSS.
3.
Non-persistent(Reflective)
XSS: These attacks are not persisted, meaning the XSS is delivered and executed
via a single request and response. Reflected attacks
are those where the injected script is reflected off the web server, such as in
an error message, search result, or any other response that includes some or all
of the input sent to the server as part of the request. Reflected attacks are
delivered to victims via another route, such as in an e-mail message, or on
some other website. When a user is tricked into clicking on a malicious link,
submitting a specially crafted form, or even just browsing to a malicious site,
the injected code travels to the vulnerable web site, which reflects the attack
back to the user’s browser. The browser then executes the code because it came
from a “trusted” server. Reflected XSS is also sometimes referred to as
Non-Persistent or Type-II XSS.
4.
Mutated
XSS (mXSS):
Mutated XSS happens when the attacker injects
something that is seemingly safe, but rewritten and modified by the browser,
while parsing the markup. This makes it extremely hard to detect or sanitize
within the websites application logic. An example is rebalancing unclosed
quotation marks or even adding quotation marks to unquoted parameters on
parameters to CSS font-family.
What are the consequences of XSS attack?:-
From
these examples and attack vectors, it is clear that a successful XSS attack on
a vulnerable web application gives attackers a very powerful tool. With XSS,
attackers have the capability to:
 ·
Read any data and perform arbitrary
actions by impersonating the user. Such actions may include posting on social
media or conducting banking transactions.
·
Read any data and perform arbitrary
actions by impersonating the user. Such actions may include posting on social
media or conducting banking transactions.
·
Intercept user input.
·
Deface web pages.
·
Inject malicious code into web pages.
Such functionality may be reminiscent of Trojans, including fake forms for
entering credentials or paying for online orders.
Cross-site
scripting attacks can also be leveraged for financial benefit in more indirect
ways. For example, severe XSS attacks can be used to embed advertising
information or manipulate Internet ratings through DOM modification.
Impact
typically depends on the type of XSS vulnerability (for example, stored or
reflected), difficulty of implementation, and whether it requires
authentication (perhaps not everybody has access to the page in question).Other
factors include what, if any, additional actions are required from the user;
whether the attack is triggered reliably; and what exactly could a potential
attacker gain. If the site does not contain private information (because of
there being no authentication or distinction between users), then the impact is
minimal.
The XSS Vulnerabilities is divided into three categories :-
·
Low – Vulnerabilities on routers or
other local devices requiring authorization. XSS here requires privileged user
rights, or, roughly speaking, self-XSS. Since the difficulty of an attack is
relatively high, the resulting impact is small.
·
Medium – Here we refer to all
reflected and stored XSS attacks that require visiting a certain page (social
engineering). This is more critical and has a greater impact, since stored XSS
is easier for attackers. But because the user must still log in first, the
criticality is not so high.
·
High – In this case, the user
independently visits a page that contains a malicious script. Some examples are
XSS in a personal message, a blog comment, or an admin panel that appears
immediately after login (in the user list via username or in logs through user agent).
A
website might have stored XSS, resulting in High impact. However, if you need a
certain level of access to visit that site, then the impact is reduced to
Medium.It's
also important to mention that in any case, impact depends on the author's
assessment of criticality—researchers have their own viewpoints. XSS
vulnerabilities can be of high severity, but typically they receive scores
below those given to other types of attacks.
Comments
Post a Comment