Nmap is one of the most commonly used tools by ethical hackers. Its ease of use and clean installation along with powerful scanning options, adds to its popularity. This nmap tutorial gives you a comprehensive understanding of the tool and teaches you how to perform advanced scans by yourself.
Below is the list of topics that I’ll be covering through the course of this nmap tutorial.
- What is Nmap?
- Nmap Scan Types
- Nmap Command List
What is Nmap?
Nmap, short for Network Mapper, is a network discovery and security auditing tool. It is known for its simple and easy to remember flags that provide powerful scanning options. Nmap is widely used by network administrators to scan for:
- Open ports and services
- Discover services along with their versions
- Guess the operating system running on a target machine
- Get accurate packet routes till the target machine
- Monitoring hosts
Nmap is a free and open source utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts.
What Does Nmap Do?
At a practical level, Nmap is used to provide detailed, real-time information on your networks, and on the devices connected to them.
The primary uses of Nmap can be broken into three core processes. First, the program gives you detailed information on every IP active on your networks, and each IP can then be scanned. This allows administrators to check whether an IP is being used by a legitimate service, or by an external attacker.
Secondly, Nmap provides information on your network as a whole. It can be used to provide a list of live hosts and open ports, as well as identifying the OS of every connected device. This makes it a valuable tool in ongoing system monitoring, as well as a critical part of pentesting. Nmap can be used alongside the Metasploit framework, for instance, to probe and then repair network vulnerabilities.
Thirdly, Nmap has also become a valuable tool for users looking to protect personal and business websites. Using Nmap to scan your own web server, particularly if you are hosting your website from home, is essentially simulating the process that a hacker would use to attack your site. “Attacking” your own site in this way is a powerful way of identifying security vulnerabilities.
How To Use Nmap
Nmap is straightforward to use, and most of the tools it provides are familiar to system admins from other programs. The advantage of Nmap is that it brings a wide range of these tools into one program, rather than forcing you to skip between separate and discrete network monitoring tools.
In order to use Nmap, you need to be familiar with command-line interfaces. Most advanced users are able to write scripts to automate common tasks, but this is not necessary for basic network monitoring.
How To Install Nmap
The process for installing Nmap is easy but varies according to your operating system. The Windows, Mac, and Linux versions of the program can be downloaded here.
- For Windows, Nmap comes with a custom installer (namp<version>setup.exe). Download and run this installer, and it automatically configures Nmap on your system.
- On Mac, Nmap also comes with a dedicated installer. Run the Nmap-<version>mpkg file to start this installer. On some recent versions of macOS, you might see a warning that Nmap is an “unidentified developer”, but you can ignore this warning.
- Linux users can either compile Nmap from source or use their chosen package manager. To use apt, for instance, you can run Nmap –version to check if Nmap is installed, and sudo apt-get install Nmap to install it.
How To Run a Ping Scan
One of the most basic functions of Nmap is to identify active hosts on your network. Nmap does this by using a ping scan. This identifies all of the IP addresses that are currently online without sending any packers to these hosts.
To run a ping scan, run the following command:
- # nmap -sp 192.100.1.1/24
This command then returns a list of hosts on your network and the total number of assigned IP addresses. If you spot any hosts or IP addresses on this list that you cannot account for, you can then run further commands (see below) to investigate them further.
How To Run A Host Scan
A more powerful way to scan your networks is to use Nmap to perform a host scan. Unlike a ping scan, a host scan actively sends ARP request packets to all the hosts connected to your network. Each host then responds to this packet with another ARP packet containing its status and MAC address.
To run a host scan, use the following command:
- # nmap -sp <target IP range>
This returns information on every host, their latency, their MAC address, and also any description associated with this address. This can be a powerful way of spotting suspicious hosts connected to your network.
If you see anything unusual in this list, you can then run a DNS query on a specific host, by using:
- # namp -sL <IP address>
This returns a list of names associated with the scanned IP. This description provides information on what the IP is actually for.
How To Use Nmap in Kali Linux
Using Nmap in Kali Linux can be done in an identical way to running the program on any other flavor of Linux.
That said, there are advantages to using Kali when running Nmap scans. Most modern distros of Kali now come with a fully-features Nmap suite, which includes an advanced GUI and results viewer (Zenmap), a flexible data transfer, redirection, and debugging tool (Ncat), a utility for comparing scan results (Ndiff), and a packet generation and response analysis tool (Nping).
Nmap Commands
Most of the common functions of Nmap can be executed using a single command, and the program also uses a number of ‘shortcut’ commands that can be used to automate common tasks.
Here is a quick run-down:
1. Ping Scanning
As mentioned above, a ping scan returns information on every active IP on your network. You can execute a ping scan using this command:
- #
2. Port Scanning
There are several ways to execute port scanning using Nmap. The most commonly used are these:
- # sS TCP SYN scan
- # sT TCP connect scan
- # sU UDP scans
- # sY SCTP INIT scan
- # sN TCP NULL
The major differences between these types of scans are whether they cover TCP or UDP ports and whether they execute a TCP connection. Here are the basic differences:
- The most basic of these scans is the sS TCP SYN scan, and this gives most users all the information they need. It scans thousands of ports per second, and because it doesn’t complete a TCP connection it does not arouse suspicion.
- The main alternative to this type of scan is the TCP Connect scan, which actively queries each host, and requests a response. This type of scan takes longer than a SYN scan, but can return more reliable information.
- The UDP scan works in a similar way to the TCP connect scan but uses UDP packets to scan DNS, SNMP, and DHCP ports. These are the ports most frequently targeted by hackers, and so this type of scan is a useful tool for checking for vulnerabilities.
- The SCTP INIT scan covers a different set of services: SS7 and SIGTRAN. This type of scan can also be used to avoid suspicion when scanning an external network because it doesn’t complete the full SCTP process.
- The TOP NULL scan is also a very crafty scanning technique. It uses a loophole in the TCP system that can reveal the status of ports without directly querying them, which means that you can see their status even where they are protected by a firewall.
3. Host Scanning
Host scanning returns more detailed information on a particular host or a range of IP addresses. As mentioned above, you can perform a host scan using the following command:
- # nmap -sp <target IP range>
4. OS Scanning
OS scanning is one of the most powerful features of Nmap. When using this type of scan, Nmap sends TCP and UDP packets to a particular port, and then analyze its response. It compares this response to a database of 2600 operating systems, and return information on the OS (and version) of a host.
To run an OS scan, use the following command:
- nmap -O <target IP>
5. Scan The Most Popular Ports
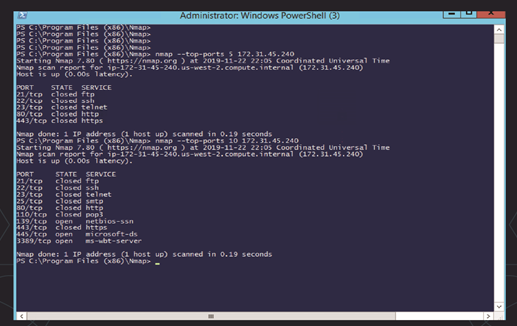
If you are running Nmap on a home server, this command is very useful. It automatically scans a number of the most ‘popular’ ports for a host. You can run this command using:
- nmap --top-ports 20 192.168.1.106
Replace the “20” with the number of ports to scan, and Nmap quickly scans that many ports. It returns a concise output that details the status of the most common ports, and this lets you quickly see whether you have any unnecessarily open ports.
6. Output to a File
If you want to output the results of your Nmap scans to a file, you can add an extension to your commands to do that. Simply add:
- -oN output.txt
To your command to output the results to a text file, or:
- -oX output.xml
To output to an XML.
7. Disable DNS Name Resolution
Finally, you can speed up your Nmap scans by using the -n parameter to disable reverse DNS resolution. This can be extremely useful if you want to scan a large network. For example, to turn off DNS resolution for the basic ping scan mentioned above, add -n:
- # nmap -sp -n 192.100.1.1/24
Nmap Scan Types
A variety of scans can be performed using Nmap. Below are the types of scans:
TCP SCAN
A TCP scan is generally used to check and complete a three-way handshake between you and a chosen target system. A TCP scan is generally very noisy and can be detected with almost little to no effort. This is “noisy” because the services can log the sender IP address and might trigger Intrusion Detection Systems.
UDP SCAN
UDP scans are used to check whether there is any UDP port up and listening for incoming requests on the target machine. Unlike TCP, UDP has no mechanism to respond with a positive acknowledgment, so there is always a chance for a false positive in the scan results. However, UDP scans are used to reveal Trojan horses that might be running on UDP ports or even reveal hidden RPC services. This type of scan tends to be quite slow because machines, in general, tend to slow down their responses to this kind of traffic as a precautionary measure.
SYN SCAN
This is another form of TCP scan. The difference is unlike a normal TCP scan, nmap itself crafts a syn packet, which is the first packet that is sent to establish a TCP connection. What is important to note here is that the connection is never formed, rather the responses to these specially crafted packets are analyzed by Nmap to produce scan results.
ACK SCAN
ACK scans are used to determine whether a particular port is filtered or not. This proves to be extremely helpful when trying to probe for firewalls and their existing set of rules. Simple packet filtering will allow established connections (packets with the ACK bit set), whereas a more sophisticated stateful firewall might not.
FIN SCAN
Also a stealthy scan, like the SYN scan, but sends a TCP FIN packet instead. Most but not all computers will send an RST packet (reset packet) back if they get this input, so the FIN scan can show false positives and negatives, but it may get under the radar of some IDS programs and other countermeasures.
NULL SCAN
Null scans are extremely stealthy scan and what they do is as the name suggests — they set all the header fields to null. Generally, this is not a valid packet and a few targets will not know how to deal with such a packet. Such targets are generally some version of windows and scanning them with NULL packets may end up producing unreliable results. On the other hand, when a system is not running windows this can be used as an effective way to get through.
XMAS SCAN
Just like null scans, these are also stealthy in nature. Computers running windows will not respond to Xmas scans due to the way their TCP stack is implemented. The scan derives its name from the set of flags that are turned on within the packet that is sent out for scanning. XMAS scans are used to manipulate the PSH, URG and FIN flags that can be found in the TCP header.
RPC SCAN
RPC scans are used to discover machines that respond to Remote Procedure Call services (RPC). RPC allows commands to be run on a certain machine remotely, under a certain set of connections. RPC service can run on an array of different ports, hence, it becomes hard to infer from a normal scan whether RPC services are running or not. It is generally a good idea to run an RPC scan from time to time to find out where you have these services running.
IDLE SCAN
IDLE scan is the stealthiest of all scans discussed in this nmap tutorial, as the packets are bounced off an external host. Control over the host is generally not necessary, but the host needs to meet a specific set of conditions. It is one of the more controversial options in Nmap since it only has a use for malicious attacks.
Nmap Commands
In this section of Nmap Tutorial, I’ll be listing down the various commands you can use in Nmap along with their flag and usage description with an example on how to use it.
Scanning Techniques
| Flag | Use | Example |
| -sS | TCP syn port scan | nmap -sS 192.168.1.1 |
| -sT | TCP connect port scan | nmap -sT 192.168.1.1 |
| –sU | UDP port scan | nmap –sU 192.168.1.1 |
| –sA | TCP ack port scan | nmap –sA 192.168.1.1 |
| Flag | Use | Example |
| -Pn | only port scan | nmap -Pn192.168.1.1 |
| -sn | only host discover | nmap -sn192.168.1.1 |
| -PR | arp discovery on a local network | nmap -PR192.168.1.1 |
| -n | disable DNS resolution | nmap -n 192.168.1.1 |
Port Specification
| Flag | Use | Example |
| -p | specify a port or port range | nmap -p 1-30 192.168.1.1 |
| -p- | scan all ports | nmap -p- 192.168.1.1 |
| -F | fast port scan | nmap -F 192.168.1.1 |
Service Version and OS Detection
| Flag | Use | Example |
| -sV | detect the version of services running | nmap -sV 192.168.1.1 |
| -A | aggressive scan | nmap -A 192.168.1.1 |
| -O | detect operating system of the target | nmap -O 192.168.1.1 |
Timing and Performance
| Flag | Use | Example |
| -T0 | paranoid IDS evasion | nmap -T0 192.168.1.1 |
| -T1 | sneaky IDS evasion | nmap -T1 192.168.1.1 |
| -T2 | polite IDS evasion | nmap -T2 192.168.1.1 |
| -T3 | normal IDS evasion | nmap -T3 192.168.1.1 |
| -T4 | aggressive speed scan | nmap -T4 192.168.1.1 |
| -T5 | insane speed scan | nmap -T5 192.168.1.1 |
NSE Scripts
| Flag | Use | Example |
| -sC | default script scan | nmap -sC 192.168.1.1 |
| –script banner | banner grabbing | nmap –script banner 192.168.1.1 |
IDS Evasion
| Flag | Use | Example |
| -f | use fragmented IP packets | nmap -f 192.168.1.1 |
| -D | decoy scans | nmap -D 192.168.1.1 |
| -g | use a given source port number | nmap -g 22 192.168.1.1 |

Comments
Post a Comment