Wireshark is the world's leading network traffic analyzer, and an essential tool for any security professional or systems administrator. This free software lets you analyze network traffic in real time, and is often the best tool for troubleshooting issues on your network.
Common problems that Wireshark can help troubleshoot include dropped packets, latency issues, and malicious activity on your network. It lets you put your network traffic under a microscope, and provides tools to filter and drill down into that traffic, zooming in on the root cause of the problem. Administrators use it to identify faulty network appliances that are dropping packets, latency issues caused by machines routing traffic halfway around the world, and data exfiltration or even hacking attempts against your organization.
Wireshark is a powerful tool that requires sound knowledge of networking basics. For most modern enterprises, that means understanding the TCP/IP stack, how to read and interpret packet headers, and how routing, port forwarding, and DHCP work, for example.
What does Wireshark do?
Wireshark intercepts traffic and converts that binary traffic into human-readable format. This makes it easy to identify what traffic is crossing your network, how much of it, how frequently, how much latency there is between certain hops, and so forth.
While Wireshark supports more than two thousand network protocols, many of them esoteric, uncommon, or old, the modern security professional will find analyzing IP packets to be of most immediate usefulness. The majority of the packets on your network are likely to be TCP, UDP, and ICMP.
Given the large volume of traffic that crosses a typical business network, Wireshark's tools to help you filter that traffic are what make it especially useful. Capture filters will collect only the types of traffic you're interested in, and display filters will help you zoom in on the traffic you want to inspect. The network protocol analyzer provides search tools, including regular expressions and colored highlighting, to make it easy to find what you're looking for.
Sometimes the best way to find anomalous traffic is to capture everything and establish a baseline.
History of Wireshark
Wireshark has been around since 1998, when it was invented by Gerald Combs and called Ethereal. Over the years it has received gargantuan amounts of community support and patches, and is widely accepted as the de facto network protocol analyzer available today.
Wireshark runs on all the major and most minor operating systems, including the usual Linux distros, Windows, OS X, FreeBSD, NetBSD, and OpenBSD. The program is free software, licensed GPL, and is thus free to use, share, and modify.
Wireshark as a learning tool
There are so many hands-on uses for Wireshark that it's easy to overlook what an effective learning tool it can be. Lifting up the hood of a car is the best way to understand how an internal combustion engine works, and likewise lifting the lid on network traffic and watching packets fly by — even drilling down to the byte level, and examining TCP headers — is a powerful way to learn, and teach others how the internet works.
Demystifying the motor that runs our information economy can only lead to better-informed business decisions and better government policy, not to mention a better-qualified workforce. Wireshark is already a staple of classroom curricula in many training settings, but the docs are complete enough at this point that an eager learner can easily download the network protocol analyzer, sniff their local wifi access point, and start examining traffic.
What Is Wireshark?
Wireshark is a network protocol analyzer, or an application that captures packets from a network connection, such as from your computer to your home office or the internet. Packet is the name given to a discrete unit of data in a typical Ethernet network.
Wireshark is the most often-used packet sniffer in the world. Like any other packet sniffer, Wireshark does three things:
- Packet Capture: Wireshark listens to a network connection in real time and then grabs entire streams of traffic – quite possibly tens of thousands of packets at a time.
- Filtering: Wireshark is capable of slicing and dicing all of this random live data using filters. By applying a filter, you can obtain just the information you need to see.
- Visualization: Wireshark, like any good packet sniffer, allows you to dive right into the very middle of a network packet. It also allows you to visualize entire conversations and network streams.
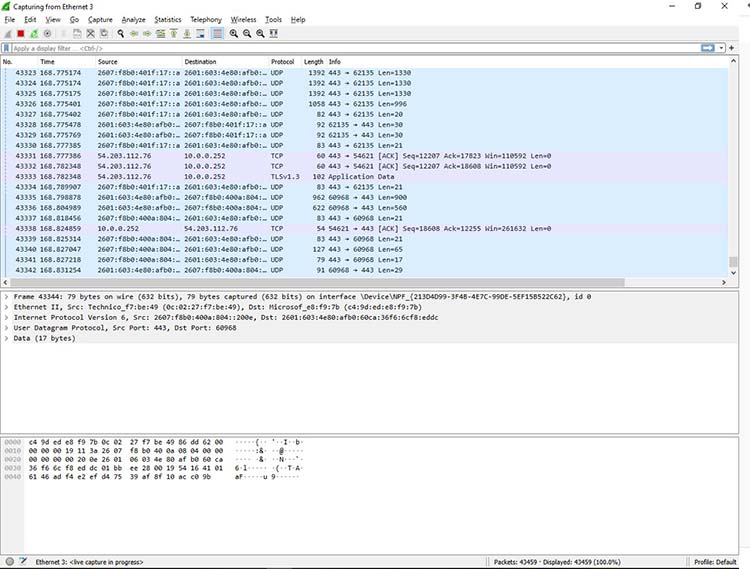
Viewing a packet capture in Wireshark
Packet sniffing can be compared to spelunking – going inside a cave and hiking around. Folks who use Wireshark on a network are kind of like those who use flashlights to see what cool things they can find. After all, when using Wireshark on a network connection (or a flashlight in a cave), you’re effectively using a tool to hunt around tunnels and tubes to see what you can see.
What Is Wireshark Used For?
Wireshark has many uses, including troubleshooting networks that have performance issues. Cybersecurity professionals often use Wireshark to trace connections, view the contents of suspect network transactions and identify bursts of network traffic. It’s a major part of any IT pro’s toolkit – and hopefully, the IT pro has the knowledge to use it.
When Should Wireshark Be Used?
Wireshark is a safe tool used by government agencies, educational institutions, corporations, small businesses and nonprofits alike to troubleshoot network issues. Additionally, Wireshark can be used as a learning tool.
Those new to information security can use Wireshark as a tool to understand network traffic analysis, how communication takes place when particular protocols are involved and where it goes wrong when certain issues occur.
Of course, Wireshark can’t do everything.
First of all, it can’t help a user who has little understanding of network protocols. No tool, no matter how cool, replaces knowledge very well. In other words, to properly use Wireshark, you need to learn exactly how a network operates. That means, you need to understand things such as the three-way TCP handshake and various protocols, including TCP, UDP, DHCP and ICMP.
Second, Wireshark can’t grab traffic from all of the other systems on the network under normal circumstances. On modern networks that use devices called switches, Wireshark (or any other standard packet-capturing tool) can only sniff traffic between your local computer and the remote system it is talking to.
Third, while Wireshark can show malformed packets and apply color coding, it doesn’t have actual alerts; Wireshark isn’t an intrusion detection system (IDS).
Fourth, Wireshark can’t help with decryption with regards to encrypted traffic.
And finally, it is quite easy to spoof IPv4 packets. Wireshark can’t really tell you if a particular IP address it finds in a captured packet is a real one or not. That requires a bit more know-how on the part of an IT pro, as well as additional software.
Common Wireshark Use Cases
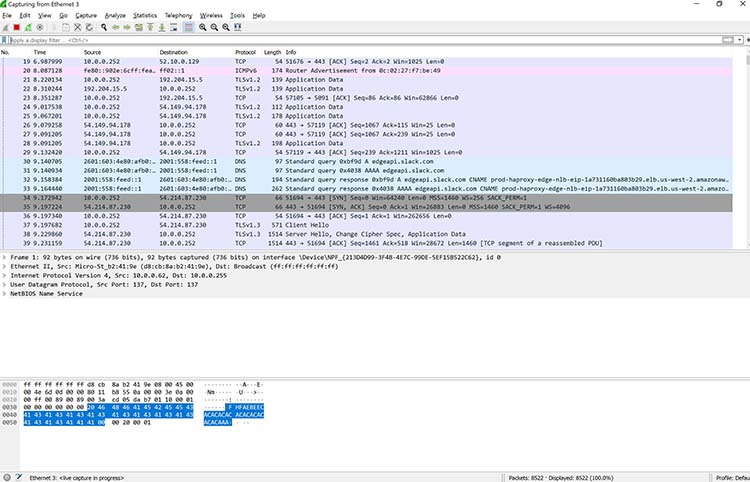
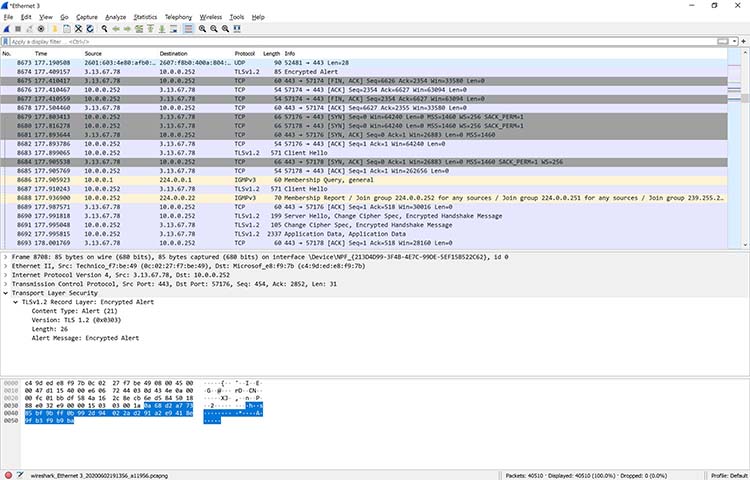
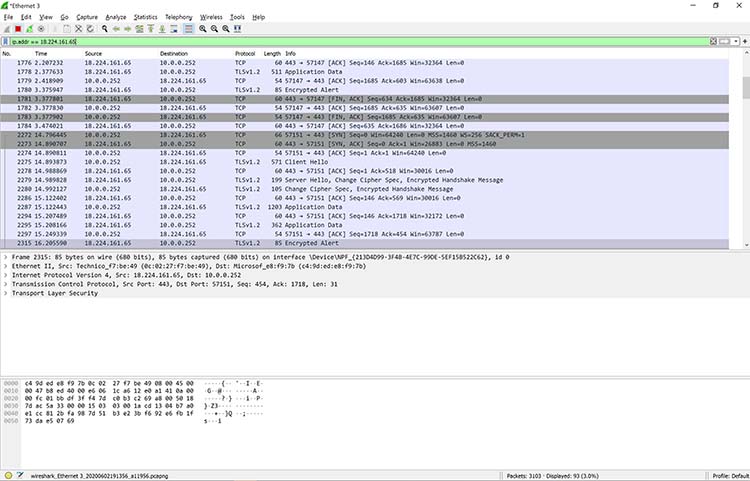
Here’s a common example of how a Wireshark capture can assist in identifying a problem. The figure below shows an issue on a home network, where the internet connection was very slow.
As the figure shows, the router thought a common destination was unreachable. This was discovered by drilling down into the IPv6 Internet Message Control Protocol (ICMP) traffic, which is marked in black. In Wireshark, any packet marked in black is considered to reflect some sort of issue.

Drilling down into a packet to identify a network problem using Wireshark
In this case, Wireshark helped determine that the router wasn’t working properly and couldn’t find YouTube very easily. The problem was resolved by restarting the cable modem. Of course, while this particular problem didn’t necessitate using Wireshark, it’s kind of cool to authoritatively finalize the issue.
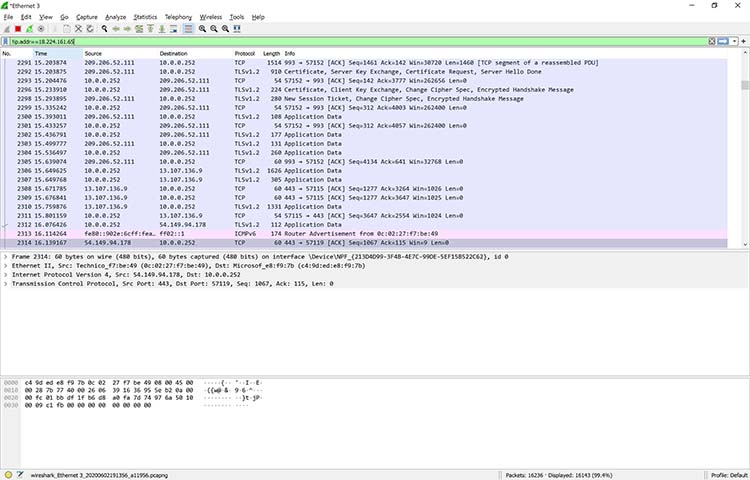
When you take another look at the bottom of Figure , you can see that a specific packet is highlighted. This shows the innards of a TCP packet that is part of a transport layer security (TLS) conversation. This is a great example of how you can drill down into the captured packet.
Using Wireshark doesn’t allow you to read the encrypted contents of the packet, but you can identify the version of TLS the browser and YouTube are using to encrypt things. Interestingly enough, the encryption shifted to TLS version 1.2 during the listening.
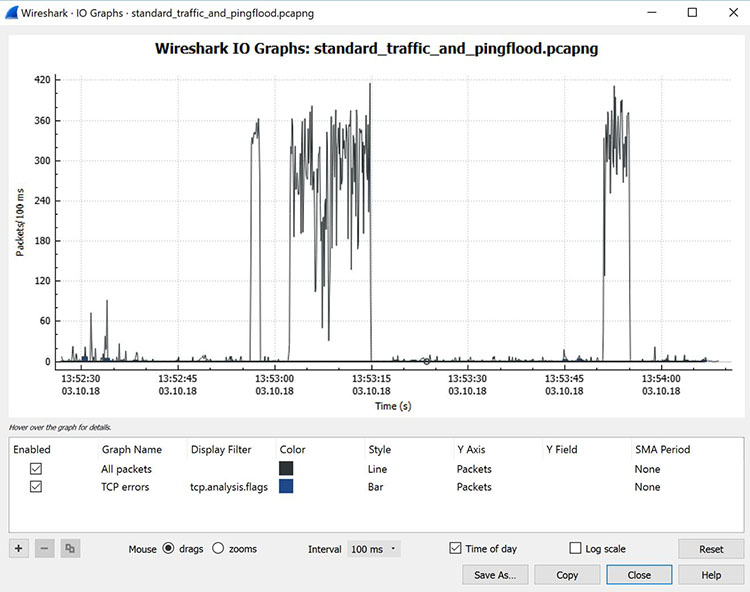
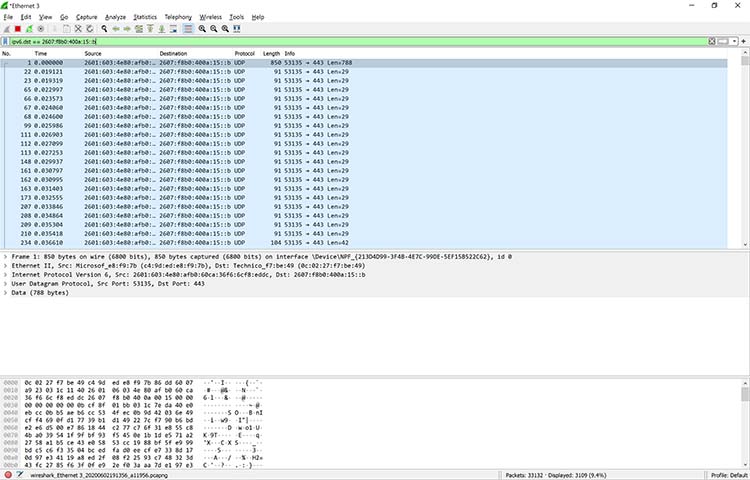
Wireshark is often used to identify more complex network issues. For example, if a network experiences too many retransmissions, congestion can occur. By using Wireshark, you can identify specific retransmission issues, as shown below in Figure.
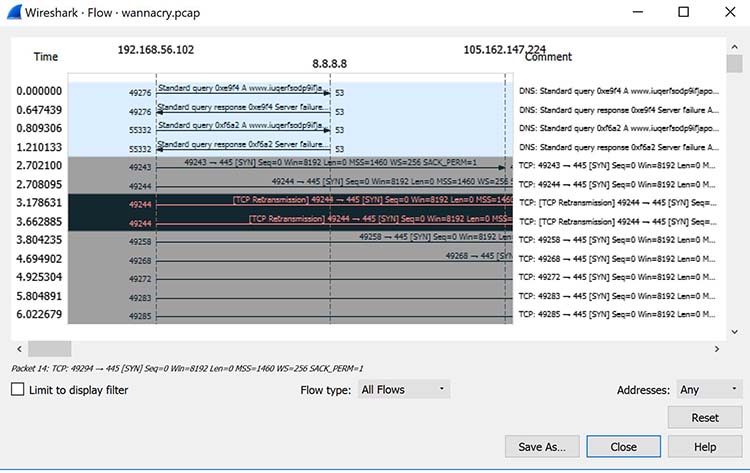 Viewing packet flow statistics using Wireshark to identify retransmissions
Viewing packet flow statistics using Wireshark to identify retransmissions
By confirming this type of issue, you can then reconfigure the router or switch to speed up traffic.
How to Use Wireshark
You can download Wireshark for free at www.wireshark.org. It’s also freely available, as an open source application under the GNU General Public License version 2.
How to Install Wireshark on Windows
If you’re a Windows operating system user, download the version appropriate for your particular version. If you use Windows 10, for example, you’d grab the 64-bit Windows installer and follow the wizard to install. To install, you’ll need administrator permissions.
How to Install Wireshark on Linux
If you have a Linux system, you’d install Wireshark using the following sequence (notice that you’ll need to have root permissions):
$ sudo apt-get install wireshark
$ sudo dpkg-reconfigure wireshark-common
$ sudo usermod -a -G wireshark $USER
$ newgrp wireshark
Once you have completed the above steps, you then log out and log back in, and then start Wireshark:
$ wireshark &
How to Capture Packets Using Wireshark
Once you’ve installed Wireshark, you can start grabbing network traffic. But remember: To capture any packets, you need to have proper permissions on your computer to put Wireshark into promiscuous mode.

Comments
Post a Comment