
Is Web App Penetration Testing Worth the Price?
The Fundamentals of Web App Penetration Testing
A couple of blog posts ago we went through the fundamentals of Web Application Penetration Testing.
We suggested that a web application penetration test is an assessment of the security of the code and the use of software and libraries on which the application runs. Pen testers are security professionals that will search for vulnerabilities in web apps such as:
- Injection vulnerabilities
- Broken authentication
- Broken authorization
- Incorrect error handling
In this blog post, we will discuss the pricing and overall economics of conducting web app penetration tests. First, as a note, from a broad perspective, a penetration test is an authorized simulated cyber-attack on a computer system or application performed to assess the strengths and weaknesses of the systems or application from that of a criminal, hacker, insider threat, and so on. One thing to remember is that a penetration test is a point-in-time test that is or should be conducted periodically as systems, applications and environments change frequently and thus, so does the security of those assets.
Penetration tests are critical to providing IT security an understanding of the overall security posture of the organization and the individual assets within the organization. It tests the security controls the organization has adopted for the sole purpose of strengthening existing controls and adding new controls to eliminate weaknesses.
Web Apps are the Most Targeted Asset by Hackers
In our previous blog post, we touch on some of this information so why the review? Because web apps are by far the most targeted asset cybercriminals use to access systems, escalated attacks, gain privileges to high priority systems and ultimately steal the sensitive data of the organization, its customers, and employees. As a matter of fact, according to SANS institute, web applications account for more than 60% of targets in cyber-attack attempts. In our opinion, this percentage is likely far higher over the past year or year and a half. Literally, tens of thousands of websites are targeted and hacked every day.
Vulnerability assessments, security posture assessments, and penetration tests are geared to evaluate the security strategy of an organization and they are critical. However, for the most part, they are not intended to specifically test the security of a web application like a pen test specifically designed to find flaws in the code that attackers can take advantage of to gain access to a system.
Determining the frequency of doing a web app pen test depends on a variety of factors including:
- Is the application business-critical?
- How often does the application’s code change?
- What are other related systemic risks to the app?
In addition, because software developers or devops are constantly publishing new code, the need for pen-testing could be fairly often. Organizations conduct web app pen tests on an as-needed basis, which can be as often as quarterly or just once a year. Typically, the frequency of pen testing is aligned with the minimum requirements for compliance such as in ISO, PCI DSS, FISMA, HIPAA, Sarbanes-Oxley, and others.
The Real Cost of a Web App Pen Test
First, we recommend using pen testers who can clearly communicate what they are testing and discuss actionable remediation. A security testing mill which you’ll find via Google pretty easily is going to cost less, but you’re not going to get the advantage of talking to an expert human who will support your IT security team’s goals to use the information to prevent future hacks.
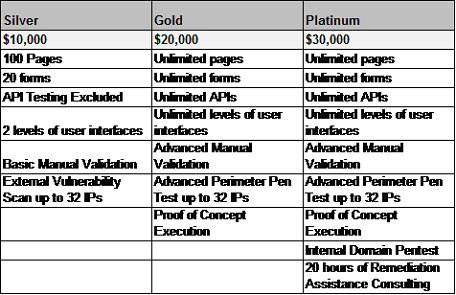
Second, a penetration test can cost anywhere from a few thousand dollars for a small, non-complex organization to more than $100,000 for a large, complex one. Penetration testing for a very “simple” single server/database web application with less than 10 pages, no publicly exposed APIs and 1-2 user roles will cost you approximately $5,000 US or thereabouts. If you are quoted an amount less than this you should ask the pen test provider serious questions about the robustness, relevance, and worth of the pen test that they are quoting you for because it might not be a quality test.
We added our pricing below which we discussed in our previous blog post and which you can always discuss with one of our experts.
Second, be careful concerning how much time a web app pen tester requires from your team including choosing a vendor, negotiating a contract, scoping the test, and finding an appropriate start date. Think about it, this can often be up to two weeks of effort you spend internally just to get a vendor to start a test. Make sure that vendor is easy to work with, can guide you based on your needs, and is 100% prepared to get started with the project on-time.
Third, when the penetration test is completed you should receive a comprehensive report that needs to include all the remediation issues that are found. These issues should be discussed and evaluated between the pentester and your team in order to prioritize fixes. In many cases, there will be several days if not a week or two of remediation that needs to be handled by your team. Remediation is of course a job on top of the jobs your team conducts on a daily basis so the easier the pen tester can spell out the issues, the faster your team can handle remediation.
Finally, verifying your team’s remediation of the vulnerabilities is generally not included in a web app pen test. Thus, you typically rely on other tools such as a Dynamic Application Security Test (DAST) scanner. However, scanners won’t learn your business logic and it won’t find that vulnerable plug-in that gives Admin access to your application.
Tests may even run a Buffer overflow or SQLi attack which will ultimately damage your web app. In addition, it will not deliver zero false positives, so there is a possibility it will increase pen test remediation activities.
Conclusion
Human Interaction is Key to a Successful Project
Pen testing as a service is becoming increasingly popular, however, the drawbacks to not having a real, live expert to discuss issues with are critical to eliminating vulnerabilities both now and in the future.
Access to Security Experts
Please make sure that human is a certified ethical hacker and an experienced expert in web app penetration testing. Further, make certain they come from an organization with a quality reputation and the ability to help you with other security needs.
Transparent Pricing is Critical
Find partners that can provide pricing in a clear, understandable manner. Lots of security services are custom and difficult to estimate, however, web app pen tests should be fairly straightforward when it comes to pricing.
Making Remediation a Priority
Detected vulnerabilities and risk-based remediation need to be available immediately after the test is complete and the report is delivered. The partnership between the pen tester, IT security, and devops should be a priority and should start as soon as possible
Comments
Post a Comment