The Difference Between a Penetration Test and Vulnerability Assessment - Part 1
What is the Difference Between a Penetration Test and Vulnerability Assessment?
Part 1 of 2
Comparing Penetration Tests and Vulnerability Assessments
The staff here at SecureOps is consistently asked the purpose and the differences between vulnerability scans, vulnerability assessments and penetration tests – including all the variations of both such as red teaming, capture the flag exercises, bug bounty programs and more. Our goal in this blog post is to work from a high level and explain the general differences between identifying vulnerabilities to a more detailed level and ultimately walk through what the services are from an execution perspective and what benefits they offer an organization in terms of improving security.
Let’s start with answering the broad question first and dig deeper from the explanation that we use here at SecureOps. Vulnerability scans search systems for known vulnerabilities using a scanner like those manufactured by Nessus, GFI LANGuard, Rapid7, Retina, Qualys. A vulnerability assessment is the process of identifying, quantifying, and prioritizing the vulnerabilities in each system, then in the entire environment. The assessment should provide a prioritized list of patches and systems that need attention as well as when they need attention. Penetration testing is quite different; a quality pen test attempts to identify weaknesses that a threat actor could exploit including poor vulnerability management processes, unpatched software vulnerabilities, ineffective security settings on systems, gaps in the layer security solution and certainly much more.
Vulnerability Assessment vs Penetration Testing Snapshot Table
| Vulnerability Assessment | Penetration Testing |
| This is the process of finding and measuring the vulnerability of a system Finds vulnerabilities and exploits them to break security controls and breach systems | Creates a list of vulnerabilities prioritized by its severity Helps in charting the path which will be taken by the attacker to take over the system(s) |
| Assessments start the process of identifying systems with security issues and their impact to the organization’s risk posture | Pen tests should be conducted after assessments and when the organization has an acceptable level of security practices and wants to identify additional vulnerabilities |
| Assessments uncover, define, identify and prioritize the vulnerabilities or security gaps in a system and organization in order to prioritize security issues. | Pen tests discover vulnerabilities with specific goals in mind. They want to know how a cybercriminal can exploit a vulnerability to breach a system or organization. |
What is Vulnerability Management?
We discussed vulnerability scans and vulnerability assessments but before we move on, we figured we should explain vulnerability management briefly because it is the overriding program that contains vulnerability scans and assessment and we don’t want the term to add further confusion. The reality for many organizations is that running a vulnerability scanner that scans the majority of critical systems and produces a thousand-page report is considered fairly typical. The vulnerability scan report has allowed IT security teams to identify missing patches and insecure configurations, however these professionals were drowning and data and had no prioritized way to apply every patch in a timely manner.
For example, two years ago WannaCry and NotPetya created turmoil in even the largest corporations around the globe. Both attacks were fueled by the leaked exploit EternalBlue —a known vulnerability for which patches had been available for several months. Just after EternalBlue, Equifax suffered one of the most infamous breaches when attackers compromised a Struts vulnerability on a critical, public-facing web server—a vulnerability that had been identified several years earlier.
The real goal of any vulnerability management program should be to minimize risks to the organization introduced by vulnerabilities. Thus, vulnerability management is the process of addressing vulnerabilities, systems, data, and business goals by priority and handling the most critical patches or other issues by priority.
The first phase of the vulnerability management process is asset discovery. Organizations should know what machines or systems are deployed on their network, which has become increasingly difficult with IoT, BYOD, the digital transformation and the continuous collection of sensitive information. The next phase is the IT security teams response based on a risk-based approach to patching. The team should consider several factors including:
- The type of data it contains – PII and other sensitive data – these systems should be prioritized
- Where the system is on the network – is it exposed more than other systems to hackers?
- What the system’s function is – is it a mail server, database, public-facing system, etc.
- Whether or not the patch in question poses a threat
By considering the four variables above you can create a risk management program that will be cost-effective and aligned with the business goals. There’s an old adage in risk management: “When everything’s is a priority, nothing is a priority.” There were over 14,000 vulnerabilities or CVE’s distributed last year so obviously it is impossible to keep up in real-time with patching requirements for every system.
Download Our Comprehensive Threat and Vulnerability Management Program Infographic here: https://www.secureops.com/resources/
What Is A Vulnerability Assessment?
A vulnerability assessment, or VA, is the process of identifying threats and vulnerabilities on a target by using automated vulnerability scanners. This sometimes includes a range of manual testing with additional tools to further evaluate the security of applications or networks and to verify vulnerabilities discovered by the scanning applications.
To be clear, a vulnerability assessment is not a scan; it is a defined “point in time” assessment with a beginning and end, unlike vulnerability management which is a continuous and evolving process. Periodic assessments are part of an overall vulnerability management program.
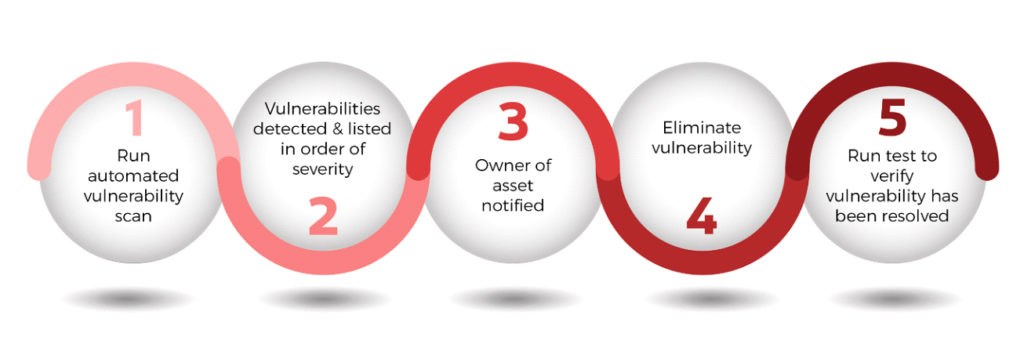
Typically, an internal or external IT security consultant will review your corporate environment and identify a variety of potentially exploitable vulnerabilities that you are exposed to in a detailed report. The report will not only list the identified vulnerabilities but also provide actionable recommendations for remediation.
By performing periodic assessments within a Vulnerability Management program, IT security can identify possible security issues that may be present on the network, both from an internal and an external perspective. Early detection introduces the opportunity to address the problems before the attackers can exploit the weakness.
To be clear, a vulnerability assessment is cyclical and proactive in order to uncover vulnerabilities and to perform prioritized, risk-based patching as part of an ongoing vulnerability management program.
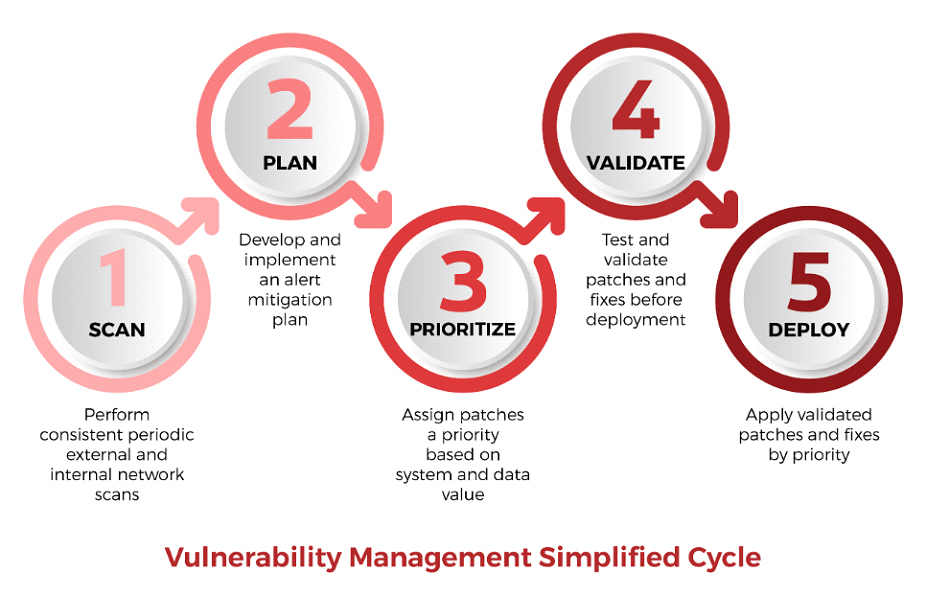
How to Perform a Vulnerability Assessment
- Install a vulnerability scanner and schedule periodic scanning – many organizations scan once per month
- Scan your company’s network to uncover potential vulnerabilities – This scan should include all devices with an IP address, such as desktops, laptops, printers, routers, switches, hubs, servers, wired and wireless networks, and firewalls.
- Identify any changes, pending updates or missing software patches – Neglecting to update your software regularly can leave your system vulnerable.
- Identify and prioritize risks – It is vital to assess your databases and identify which systems are priority – for example, those that hold PII or personal information like credit card numbers, social security numbers, and dates of birth.
- Select strategic risk-based remediation – Any thorough scan is likely to surface some vulnerabilities. Implement remediation efforts and prioritize systems with your most high-risk data.
- Plan your remediation tasks – Ensure minimal interruptions in your network’s service, and maximal convenience to your team and your clients.
This seems like a perfect place to take a quick breather before we jump into Penetration Testing and all variations and benefits. The second and final blog post on The Difference between Vulnerability Assessments and Penetration Testing will be posted shortly.

Comments
Post a Comment